Vulnerability Detection System
Everyday our devices share data on public networks. The SWAP system uses active and passive scanning techniques, determines if a device is running compromised software, and blocks it from accessing the network, bummer.
In my last year of study at the University of Pretoria we were required to produce a working prototype business ‘solution’ for a client. Our client tendered for) was the Department of Peace, Safety and Security (DPSS) at the CSIR. The Secure Wireless Access Point (SWAP) project served as a proof of concept with regards to how much information can be gathered by active vs passive scanning in digital fingerprinting of devices. Ref: SWAP Project Site
Overview
The best way to describe SWAP is a distributed, passive, vulnerability detection system deployed on geographically disparate open networks. It is divided into Access Point software and Control Point software.
The AP software works alongside a captive portal and co-resides on the access point(s), while the CP software is a web application used to configure multiple access points with fingerprinting rules.
These fingerprinting rules are used to decide whether a scanned device’s fingerprint is dangerous to the network and vulnerable to attack, in which case, is denied access and given an appropriate solution to patch the vulnerability. After the patch is applied, the device may attempt to access the network again and will undergo the fingerprint process and is again given either an ‘allow’ or ‘deny’ decision from it’s new fingerprint.
The AP software is also sub divided into co-residing pfSense networking functionality, the thin webserver and a daemon process which does all the ‘heavy lifting’.
High level component interactions:
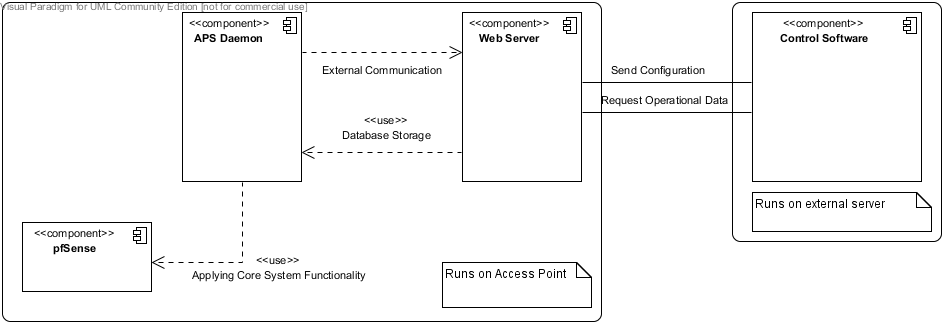
Let’s look at the access point software (AP software) and the control point software (CP software) in more detail…
Access Point Software
The Access Point Software co-resides on the access point hardware (typically a wireless router) with existing network software (we used the pfSense networking distribution) and is concerned with passively fingerprinting client wireless devices as they connect to the network, and allowing or denying access to the network and internet.
Client devices will establish a wireless connection to the Access Point and be assigned an IP Address from co-residing DHCP server but be denied any further network access by means of either firewall or routing rules.
The fingerprinting process will then take place wherein the user is interacted with via a captive portal and any identified software will be compared to the administrator-configured list of Fingerprint Rules which define vulnerable software, or a 3rd party vulnerability database. If no vulnerable software is detected, then network rules will be added to grant the device access for the duration of its DHCP lease.
The solution can thus be seen to work on ISO OSI Network Layers 4 and up, with assistance from the Access Point software to use some Layer 3 functionality, if required.
AP Software Overview
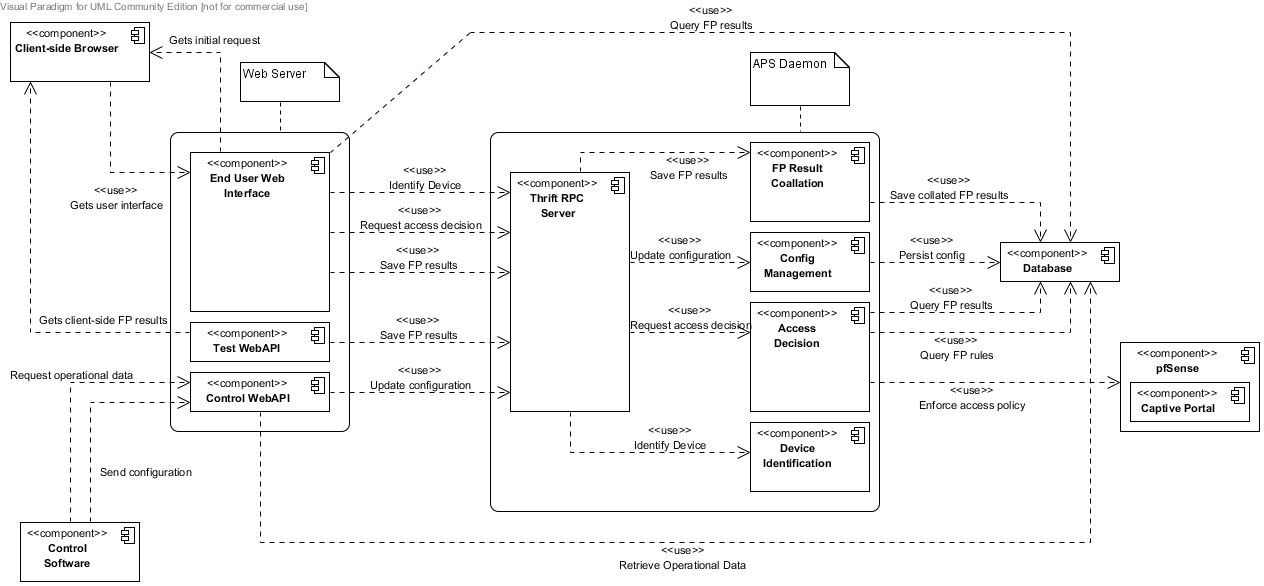
The captive portal is configured to redirect unauthenticated requests to our web server running on the access point which then begins the fingerprint process. The request opens what we call a fingerprint window which is a configurable time in which the SWAP system has to do any lookups of the client fingerprint for potential vulnerabilities.
In this window the PHP web server communicates seamlessly via a non-blocking thrift server (RPC framework) to a ++ daemon process that collates fingerprint tests from the UAS (user agent string), banner grabbing javascript code and p0f results of listening on the packet stream, the daemon then saves fingerprint results to the database.
After the fingerprinting window is complete the client device’s browser refreshes and the resulting decision from the fingerprints received within the window are shown to the user.
Notice the interaction between the Access Decision Module and pfSense’s networking functionality - this is what lets the client device on the network; also note the two API’s sitting in the web server, receiving/sending fingerprint results and configuration/operational data from the control point software.
Control Point Software
The Control Point Software serves as a central point to store, collate and present statistical and status information (from the Access Point Software), and send out relevant configuration information for one or more access points. The Control Software is a web based application which allows operators to login and perform various administrative functions in accordance with their assigned privileges.
Other noteable features include being able to kick client devices from any access point network and to view the status (DENIED/ALLOWED/PENDING) of client devices on all networks in real time in a force directed acyclic graph (a tree structure), as well as various other collated statistics.
CP Software Overview
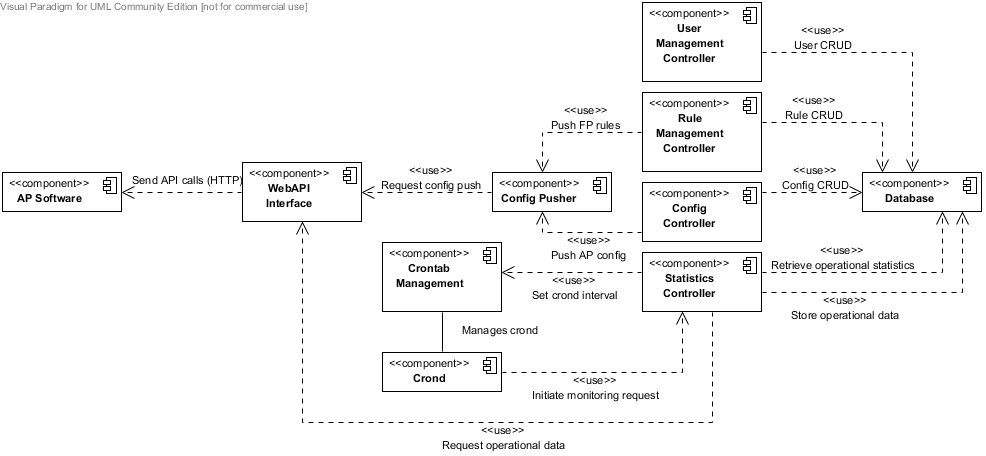
The control point software runs in a typical LAMP stack and is built upon the open source lightweight Yii MVC web framework, and provides the ability to administer one or more access point(s) configuration including system configuration, as well as custom fingerprint rules. Fingerprint rules define what identified software packages from the fingerprints are deemed ‘insecure vulnerable’.
Configuration may be applied in batches to multiple access points or individually per access point. The configurable cron job makes requests to the access point(s) ControlWebAPI to ask for new operational data in order to show various statistics about what devices are connected to the network, what are the most identified software packages etc.
Documentation & Code base
I cannot put the full documentation and code on the web because of intellectual property rights, but if you would like to know more about the system, or are interested in implementing something along the same lines, get into contact with me and I can go into more detail about our approach, architecture, choice of technologies and deployment platforms.
Conclusion
Effectively what we did was augment router software (like pfSense, OpenWRT etc) with behaviour beyond just customizing the theme of a captive portal. We added passive fingerprinting for devices that attempt to connect to the network, and took over the access control of the captive portal with the decision ALLOWED/DENIED) given to the device according to it’s fingerprint - from which we could identify vulnerable software using custom definitions of a vulnerability (MS IE version <= 7), or connecting to a 3rd party vulnerability database.
In addition, we also added management software that is able to configure these access points that may reside in geographically disparate locations, as well as view real time connected devices and other various statistics. Using the control point software, the system is capable of being deployed over a vast network of access points - think of how you would deploy the system on a university campus by setting up multiple access points over the campus enabling wifi coverage over the entire grounds, then using the control software to push the same configuration to all access points.
The beauty of the project was that ~90% of the information that may be collected using active scanning techniques, may be collected using passive scanning techniques, and by doing so, does not violate the ECT and RICA acts of South Africa which govern the management of electronic information (among other things), like some active scanning techniques do.
Questions? I’d be humbled and happy to help.